– Personal, public, and some non-public information on 191 million registered voters exposed
– Efforts to identify database’s owner to notify them unsuccessful
– Database still exposed
UPDATED Dec. 29: As of last night, the database is no longer publicly available. Yesterday, NationBuilder issued this statement.
A misconfigured database leaking the personal information of over 191 million voters was reported to DataBreaches.net by researcher Chris Vickery. This report includes some of the results of an investigation by Vickery, DataBreaches.net, and Steve Ragan of Salted Hash.
Backgrounder: What Data Are in a Voter’s List?
Voter lists or databases may include a lot of information about you in addition to the information you are required to provide when you first register as a voter. They may contain your first and last name, your home and mailing addresses, your date of birth, gender, and ethnicity, the date you registered to vote, your telephone number, your party affiliation, your e-mail address if you provided one when you registered, your state voter ID, whether you’re a permanent absentee voter, and whether or not you’re on the Do Not Call list.
Lists of voter registration information may be obtained from your state and then combined with other data sources by marketing firms or those serving as consultants to political parties or political campaigns. Who can obtain the state’s voter list, and how it may be used depends on the state’s laws. So databases developed for political campaigns may also include whether or not you voted in the last general and primary elections, whether you appeared to follow a party line vote, and there may be a score predicting whether you’re likely to vote in an upcoming election or for a particular party or candidate. Databases developed for issue-oriented campaigns or non-profits doing fundraising may contain even more personal information such as your religious affiliation, whether you’re likely to be anti-abortion, whether you’re a gun owner, etc.
While the majority of states make their voter registration lists available as a matter of public record and do not restrict use, some states restrict use. For example, South Dakota requires the requestor of voter registration data to sign a statement:
“In accordance with SDCL 12-4-41, I understand that the voter registration data obtained from the statewide voter registration database may not be used or sold for any commercial purpose and may not be placed for unrestricted access on the internet.”
In California, information on voter registration cards is considered confidential, and subject to many restrictions to access and use. One of the restrictions is that the information may not be made available to persons outside the U.S. And in Hawaii, voter registration information may only be used for elections and by the government.
But for the most part, not only can political organizations acquire information about you, they may be able to post it publicly, or even create an app with the information.
Not surprisingly, the more complete the list or database, the more costly it may be. A database with information on all American voters, for example, might go for about $270,000, according to one marketing firm consulted by researcher Chris Vickery.
Voter lists have a number of recognized uses. Even though a percentage of the records are likely to contain inaccuracies, these databases are a goldmine of potential voters for political parties and campaigns, as well as pollsters. The recent political flap when some of Bernie Sanders’ staffers accessed the Clinton campaign’s data shows how highly prized such information is for political purposes. Voter lists or databases also provide a treasure trove of leads for non-profit organizations doing fund-raising, and they are a valuable resource for journalists investigating election issues or candidates, for scholars, and for the government itself.
Researcher Chris Vickery Uncovers a Gold Mine
On December 20, researcher Chris Vickery contacted DataBreaches.net to say he had found a database with 191,337,174 million Americans’ voter information exposed due to a misconfiguration of the database.
He admits he got quite a shock when he found his own information in it, and sent along this screenshot:
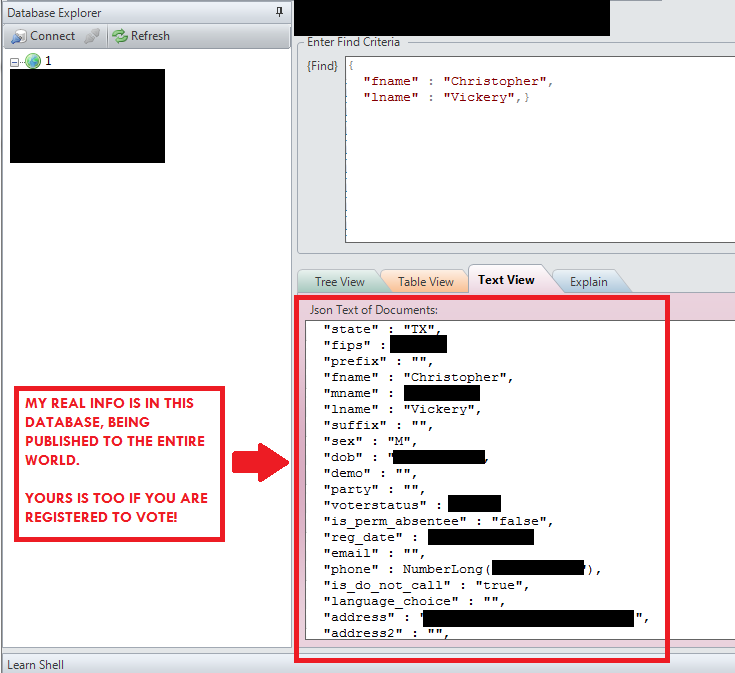
Chris wasn’t the only to get a rude shock. “Sam,” a police officer known to DataBreaches.net who asked that we not use his last name, was also concerned when DataBreaches.net showed him accurate details on himself.* To protect his and his family’s safety, Sam does not have a publicly listed phone number or address. When shown the information on him in the database, Sam’s response was “Oh man. … I deal with criminals every day who know my name. The thought of some vindictive criminal being able to go to this site and get my address makes me uncomfortable. I’m also annoyed that people can get my voting record. Whether I vote Republican or Democratic should be my private business.”
While states may suppress police officers’ voter registration records if they individually request it, it appears that there is no uniform automatic suppression of law enforcement personnel’s records in publicly available voter registration lists.
Thankfully, there are no Social Security numbers, driver’s license numbers, or any financial information in this particular database, but full name, date of birth, and address and phone number with political party and other fields – are problematic enough when it comes to protecting our privacy and security.
To see an almost-complete list of the data fields in this leaky database so you can find out what information about you may now be publicly available, see a redacted entry, here.
Who Dunnit?
Based on preliminary investigation by Vickery and DataBreaches.net of some data field labels that looked like they might be unique or proprietary, DataBreaches.net reached out to Nation Builder, the online service of 3dna, Corp., to inquire if the database was one of their databases or if it might be one of their clients’ databases. But after 24 hours with no response, and although we really wanted to know who had left this database available to the entire world, Vickery and DataBreaches.net agreed to turn to law enforcement who might be able to get the database removed or secured more quickly.
Both the FBI NY field office and IC3 were contacted, as was the California Attorney General’s Office. California was contacted as they are one of the states that restrict what cannot be disclosed. When one of their attorneys asked, “Well how much data are we talking about?” and I read her the list of data fields and told her that we had access to voter records of over 17 million California voters, her response was “Wow,” and she promptly forwarded the matter to the head of their e-crime division. The California Attorney General’s Office has not replied to follow-up e-mail inquiries since then, however, and the FBI would not comment when DataBreaches.net tried to follow up with them to find out what, if anything, they were doing.
When DataBreaches.net eventually reached someone at Nation Builder. Ben Handzo, Product Director, followed up and reported that the IP address was not one of their IP addresses. Nor, he said, was it an IP address for any of their hosted clients. Although we were – and remain – pretty certain that the database involves Nation Builder’s data because of unique data field labels and because the numbers match their database as it was in March, 2014, we had hit a dead end there. Could Nation Builder reach out to all of their customers to ask them to check to see if they were the source of the leak? Yes, but we realize that they’re really under no obligation to do so.
Meanwhile, based on the “User” in the leaky database, DataBreaches.net also reached out to a congressman’s PAC to inquire whether it might be their database. To date, they have not responded, but a staffer for the congressman said it was unlikely to be theirs as they only worked regionally and not nationally.
Enter Steve Ragan of Salted Hash, who offered to put on his deerstalker hat to help investigate after we reached out to him.
Steve began contacting some big political consulting and software firms, as he reports today over on Salted Hash. So far, none of those leads has resulted in identifying the owner of the leaky database.
Potential for Abuse?
More than one week after Vickery first discovered the leak and we began trying to locate the responsible party, the database remains online and exposed – despite countless hours on our part trying to track this leak down.
If you are a registered voter, we cannot offer you reassurance that your details have not been obtained and won’t be misused. We don’t know for how long this database has been left unsecured and how many people may have accessed and downloaded it. At this point, all we’re pretty sure of is that the data in the database include data from Nation Builder. Could it be one of their non-hosted clients leaking the database? Maybe. Could it be that someone hacked one of their clients and stored a copy of the database at this IP address? Maybe. Could it be that an employee of a client decided to make themselves a copy for their own purposes? Maybe. The possibilities are numerous. We really don’t know and DataBreaches.net declines to speculate.
Head on over to Salted Hash to get Steve Ragan’s report and insights.
And then maybe call your Senator and Representative in Congress and tell them that as a constituent, you want them to ensure that there are adequate laws protecting the privacy of our information. It’s too easy to upload a database with all of our contact details, our date of birth, and our political affiliations and voting history to the Internet where anyone can grab it. Tweet them a link to this article with #ProtectMyPrivacy.
Do You Know?
And if anyone has any knowledge of who might be responsible for this database, please contact [email protected] or contact me on Twitter or WICKR (“PogoWasRight”). For encrypted tips by e-mail, my OpenGPG key: 0x0625E4BA.
DataBreaches.net, Chris Vickery, and Steve Ragan will keep investigating this leak and will update our reports as more information becomes available.
—
* N.B.: Sam’s data was only retrieved from the database after Sam was asked for, and gave, his permission to do so.
This story originally appeared on DataBreaches.net.